Hey Cats 🐱💻, Today in this article we are going disscuss about how to
recover permanently deleted or lost files using foremost forensic tools; even
it can recover files from formatted media drives.
Foremost is a very useful open-source forensic utility that is able to recover
deleted files using the technique called
data carving. The
utility was originally developed by the
United States Air Force Office of Special Investigations and is able to
recover several file types like videos, office-files. images, pdf and etc.
It's also support for specific file types can be added by the user via the
configuration file. The program can also work on partition images produced by
DD or similar tools. This tool is very effective for forensic use like
recovering any data from a criminal's pen drive.
Since foremost is already present in all the major Linux distributions
repositories, So installing it is a very easy task. All we have to do is to
use our favorite distribution package manager. On Debian we can use apt.
$ sudo apt install foremost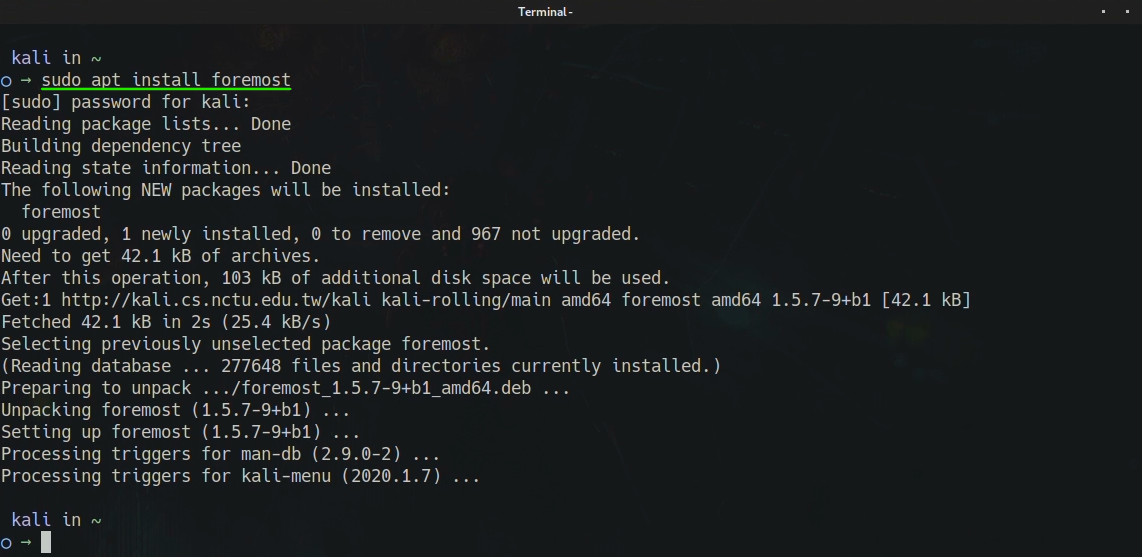
Now it's time to recover our permanently deleted data. If we need to recover
permanently deleted data from a pen drive we need to know the pen drive's
disk path. So, applying this command.
$ sudo fdisk -l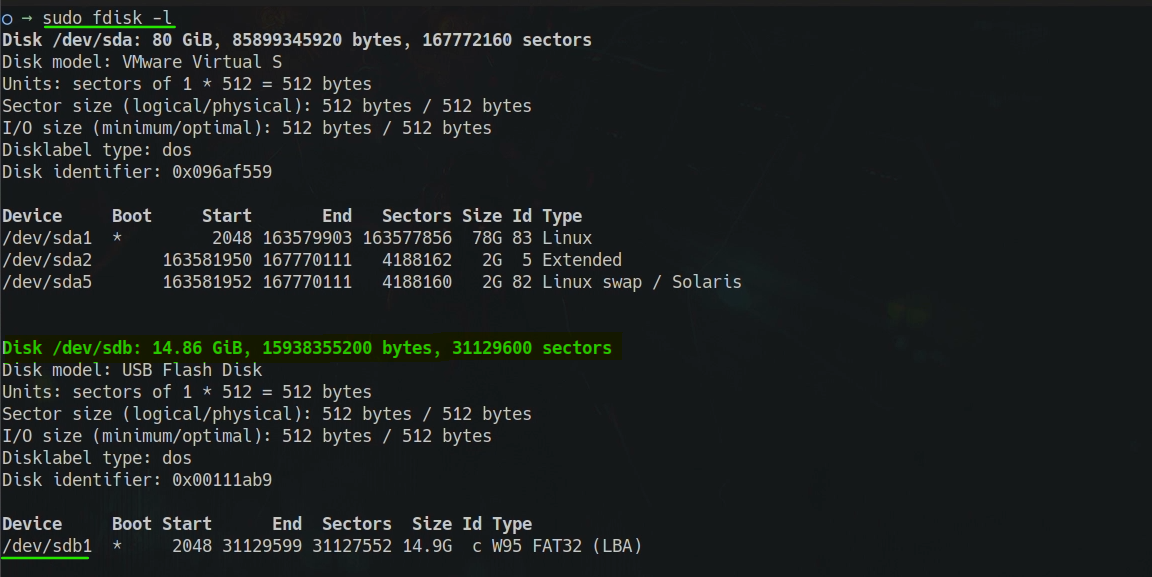
Here we can see our pen drive's location is
/dev/sdb and the main
partition of our pen drive is /dev/sdb1. This /dev/sdb1 is
the memory storage partition. We can copy this path or just remember this.
The most basic way to use foremost is by providing a source to scan for
deleted files (it can be either a partition or an image file, like those
generated with dd). Let's see an example. We want to scan the
/dev/sdb1 partition: Before we begin, a very important thing to
remember is to never store retrieved data on the same partition we are
retrieving the data from, to avoid overwriting delete files still present on
the block device.
The command we would run is:
$ sudo foremost -i /dev/sdb1
By default, the program creates a directory called
output. Inside
this directory a subdirectory for each supported file type we are attempting
to retrieve is created. Each directory will hold the corresponding file type
obtained from the data carving process.
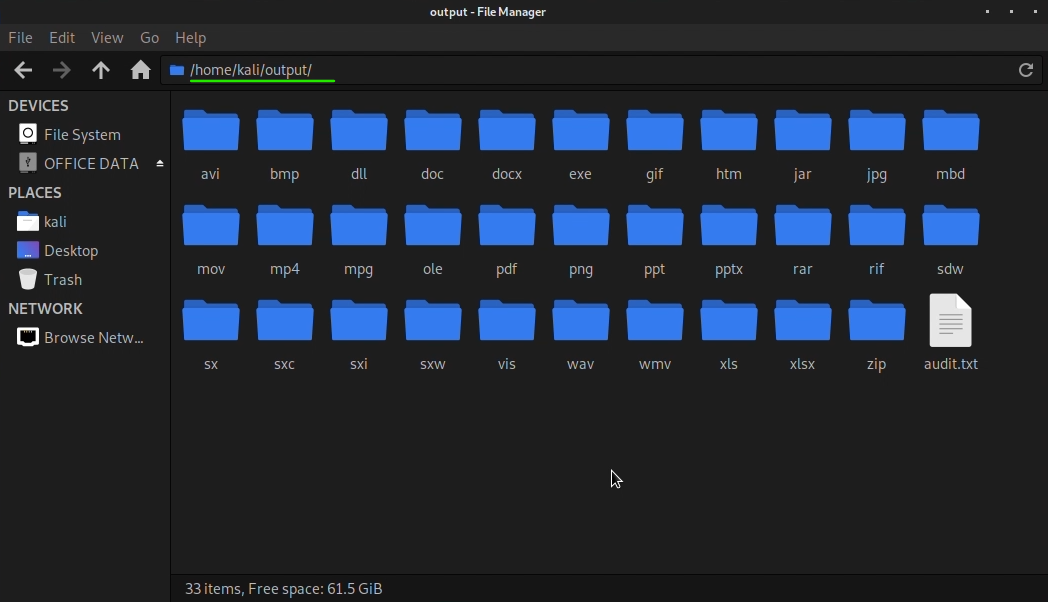
When foremost completes its job empty directories are removed. Only the
ones containing files are left on the filesystem: this lets us immediately
know what type of files were successfully retrieved. The
audit.txt file contains information about the actions performed
by the program.
By default the program tries to retrieve all the supported file types to
restrict our search we can use the
-t option and provide a list
of the file types we want to retrieve separated by a comma. In
our case, we restrict the search only to PNG and ZIP files.
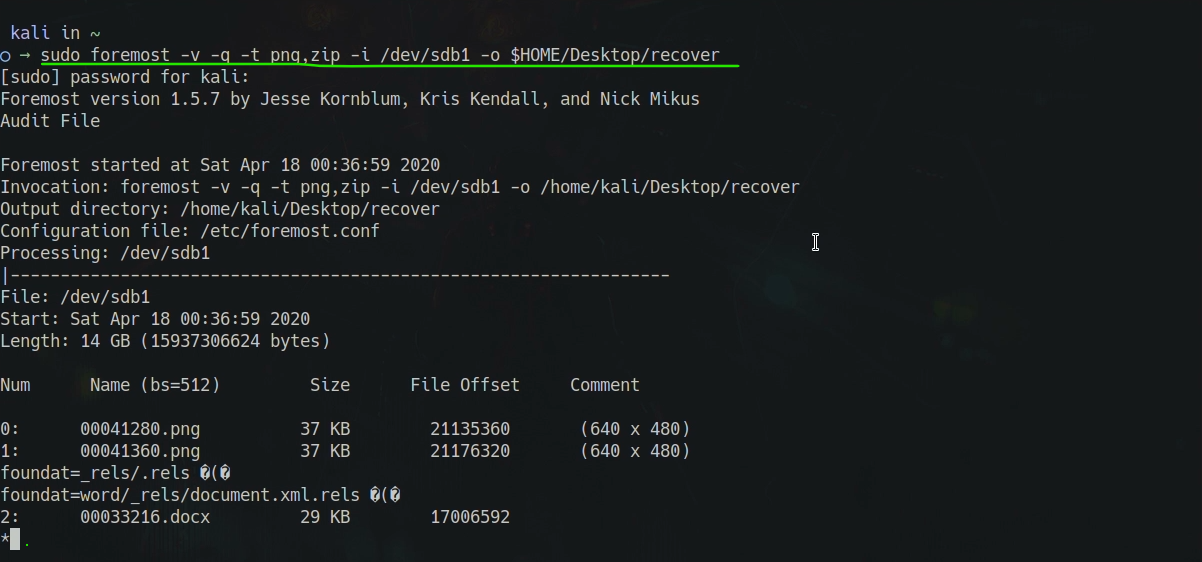
$ sudo foremost -v -q -t png,zip -i /dev/sdb1 -o $HOME/Documents/output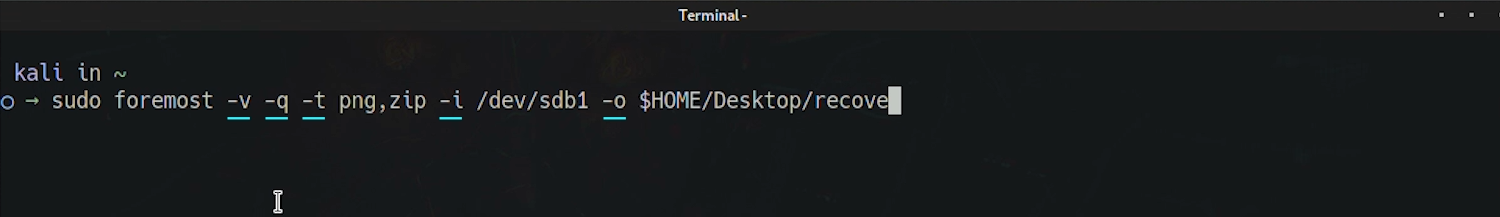
In this command we use
-t flag to specify file types; if we did
not use this foremost will recover all known file types and we choose
-v for verbose mode this mode will display all the process in
screen. We choose the -q for quick mode, -i is for
input devices in our case our input device is our pen drive and the path is
/dev/sdb1. We have also chosen -o tag to set the output
directory. That means where we want to keep our recovered files. Here we
choose the recovered folder in our Desktop. Then hit enter to start the
process.
This process will take time because it will analyze the entire disk, Small
size disks can be recovered very quickly. It also takes time if we are
recovering much data or we are not in quick mode.
Once the process complete we can check our recovered folder in Desktop.
Here we have successfully recovered our deleted data😊.
Video Tutorial
Not only in digital forensic, we can use this free tool to recover data for
our personal uses, like we can recover data from our camera memory card or any
other flash drives. We will get many paid tools for this job but when we have
a very powerful free tool; Then why do we pay for recovery tools? In
this article we have learned how to use foremost, a forensic program able to
retrieve deleted files of various types. Also we learned that the program
works by using a technique called data carving, and relies on file signatures
to achieve its goal.
Will this article was helpful? or if you have any questions or problem fell
free to ask, We always happy to help you. Don't Forget to Subscribe💖.









Post a Comment